Network Security Delivery & Monitoring
Hybrid-Cloud NIDS, NSM, NDR, & TLS/SSL Solutions
WHAT IS A NIDS, NSM, AND NDR APPLIANCE
A Network Intrusion Detection System (NIDS), Network Security Appliance (NSM), and Network Detection and Response (NDR) are critical components of modern cybersecurity architectures, each addressing different aspects of network protection. A NIDS monitors network traffic in real-time to detect malicious activities or policy violations, providing alerts for suspicious behavior based on known attack patterns or anomalies. An NSM expands on this by acting as a dedicated hardware or virtual device that integrates multiple security functions—including intrusion prevention, traffic analysis, and forensics—into a single platform, offering centralized control and visibility across the network. NDR systems take detection a step further by using advanced analytics, machine learning, and behavioral monitoring to uncover sophisticated, often stealthy threats that evade traditional defenses. They provide automated investigations, guided threat hunting, and rapid response capabilities. Together, NIDS, NSM, and NDR form a layered defense strategy, combining real-time detection, deep traffic visibility, and intelligent response to protect against known and emerging cyber threats
WHAT IS AN ENCRYPTION & DECRYPTION APPLIANCE
A Network Encryption/Decryption Appliance is a high-performance, inline device engineered to secure data in transit by encrypting outbound network traffic and decrypting inbound traffic for inspection. Built with FPGA hardware acceleration, it supports encryption standards like TLS/SSL up to 100Gbps without introducing latency. The appliance includes a secure key management system, and flexible policy controls for selective encryption or decryption based on IPs, applications, or VLANs. It operates transparently in the network, offering modes like IPsec, MACsec, or SSL/TLS while ensuring centralized management, and full integration with security monitoring systems (SIEM)
TIMELY THREAT ANALYSIS AND CONTAINMENT
Network Intrusion Detection & Forensics with/without Encrypted Traffic
01.
Full Network Transparency
- 100% network data access
- SSL/TLS traffic visibility
- Up to 100Gbps throughput
- FPGA-based solutions
- Forward/Reverse proxy
- URL filtering & Cert distribution
02.
Fast Threat Detection
- 100Gbps Suricata NIDS
- 100Gbps Clear NDR
- SIEM integration
- Fast event logging
- Log export & compression
- Northbound alerts
03.
Instant Forensics Analysis
- Event-triggered capture-to-disk
- 100Gbps full-packet capture
- Up to 720TB storage
- Out-of-box analysis software
- PCAP & Wireshark support
- Audit & Compliance
Effective Network Intrusion Detection
Today’s businesses face key challenges such as detecting unauthorized access, identifying malware or exploitation attempts in real-time, and uncovering policy violations across a network. NEOX PacketOwl acts as a Network Intrusion Detection (NIDS), a cybersecurity tool designed to monitor and analyze network traffic in real-time for signs of malicious activity, policy violations, or other security threats. It inspects north-south traffic by examining packet data and identifying suspicious patterns or anomalies that may indicate cyberattacks such as malware infections, unauthorized access attempts, or exploitation of vulnerabilities. Unlike firewalls that focus on prevention, a NIDS is primarily detection-focused, alerting administrators to potential threats so they can investigate and respond quickly


Powerful Network Security Monitoring
Enterprises, Service Providers, and Governments need real-time network visibility, consistent enforcement of security policies, and protection against a wide range of threats across complex, distributed environments.
A Network Security Monitoring (NSM) appliance like PacketOwl is designed to protect, monitor, and manage network traffic to defend against cyber threats and ensure the integrity, confidentiality, and availability of data. Positioned at key points within a network, NSM provides real-time visibility and control over network activity, enabling organizations to detect and respond to threats quickly while enforcing security policies. By simplifying management, improving threat detection, and reducing hardware sprawl, NSMs help organizations strengthen their security posture while minimizing operational complexity and cost.
Fast Network Detection and Response
Unlike traditional perimeter defenses like firewalls or antivirus systems, Network Detection and Response (NDR) focuses on identifying malicious activity within the network by analyzing traffic patterns, behaviors, and anomalies that might indicate compromised systems or insider threats. Using advanced techniques such as machine learning, behavioral analytics, and threat intelligence, NDR systems provide deep visibility into network activity, enabling security teams to uncover sophisticated attacks that may bypass conventional defenses. By offering automated alerts, threat-hunting capabilities, and detailed forensics, NEOX and Stamus Clear NDR solution plays a crucial role in enabling faster, more accurate responses to emerging threats and reducing the time attackers can dwell undetected within an organization’s environment.


Visibility into Encrypted Network Traffic
Encrypted traffic, while essential for data privacy and security, poses significant challenges for cybersecurity operations. It can hide malicious activities such as malware delivery, command-and-control communication, and data exfiltration from traditional security tools like firewalls, IDS/IPS, NSM, and NDR, which are unable to inspect encrypted payloads without decryption. This blind spot makes it harder to detect and respond to threats in real time. A Network Traffic Decryption appliance like NEOX PacketShark, is a specialized device that intercepts, decrypts, and inspects TLS/SSL encrypted network traffic to reveal hidden threats, enforce security policies, and maintain visibility across encrypted communications. After inspection, the appliance re-encrypts the traffic before forwarding it to its destination, ensuring data integrity and confidentiality. As a result, organizations can balance the need for visibility with maintaining trust and efficiency.
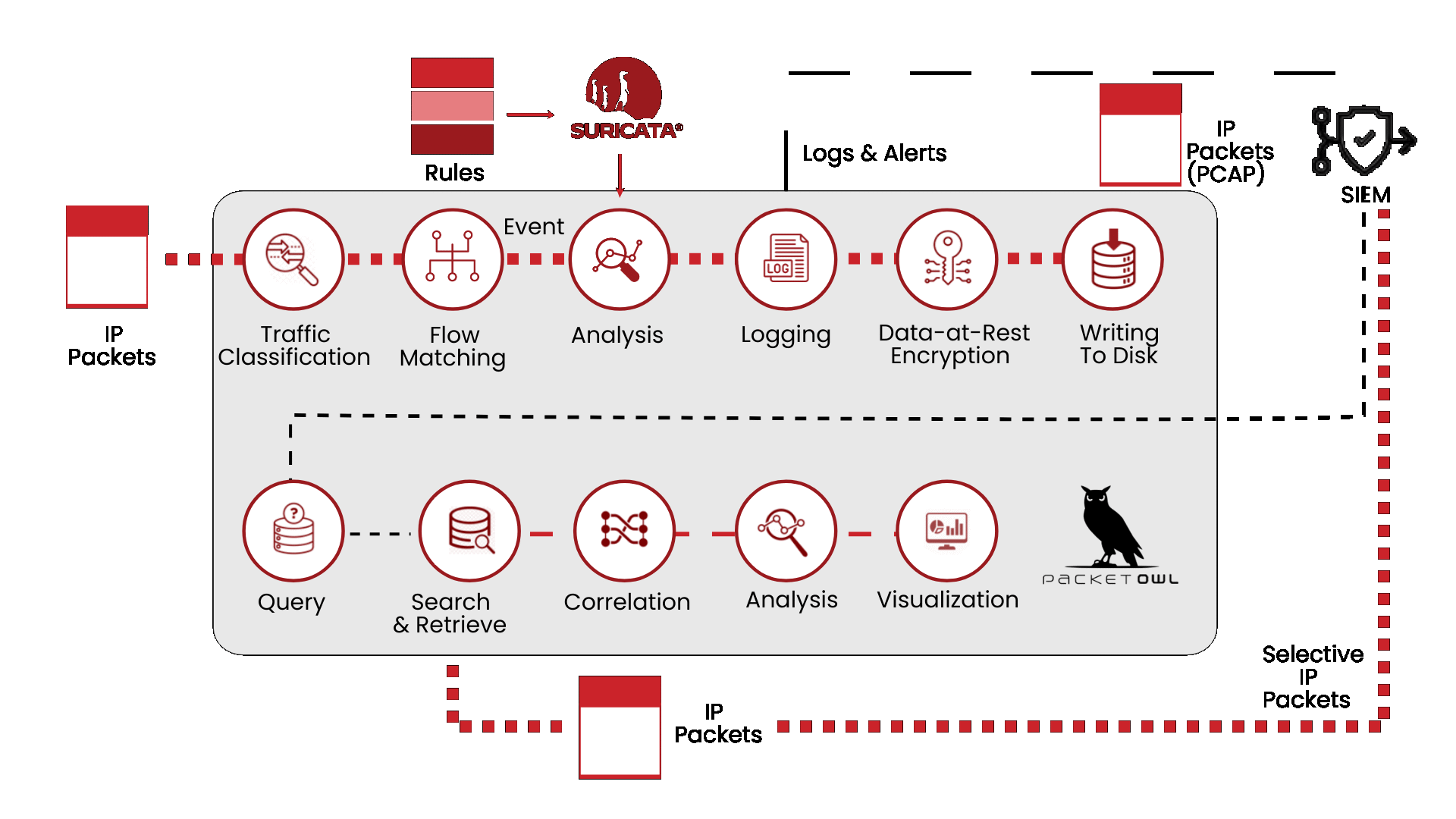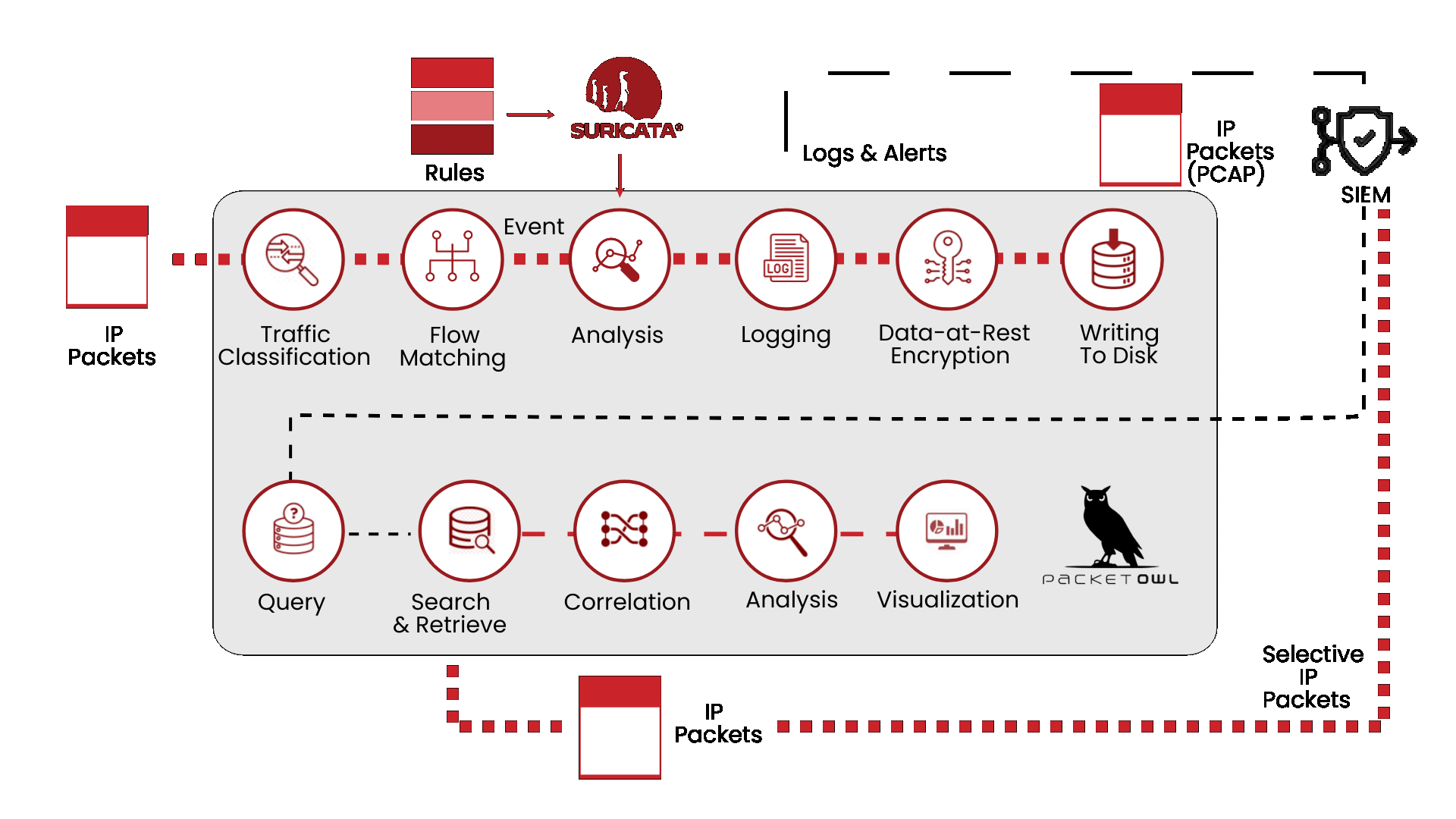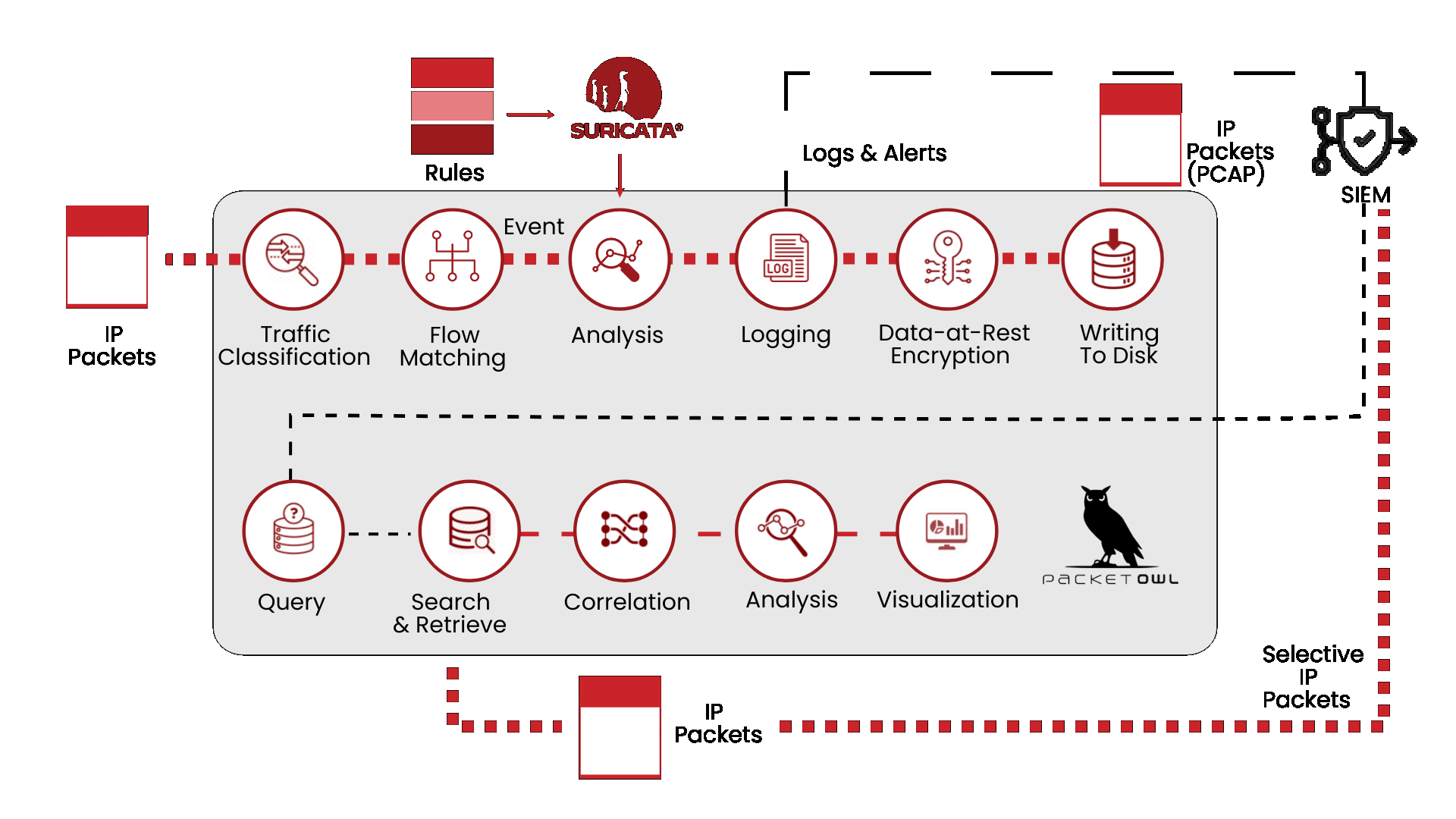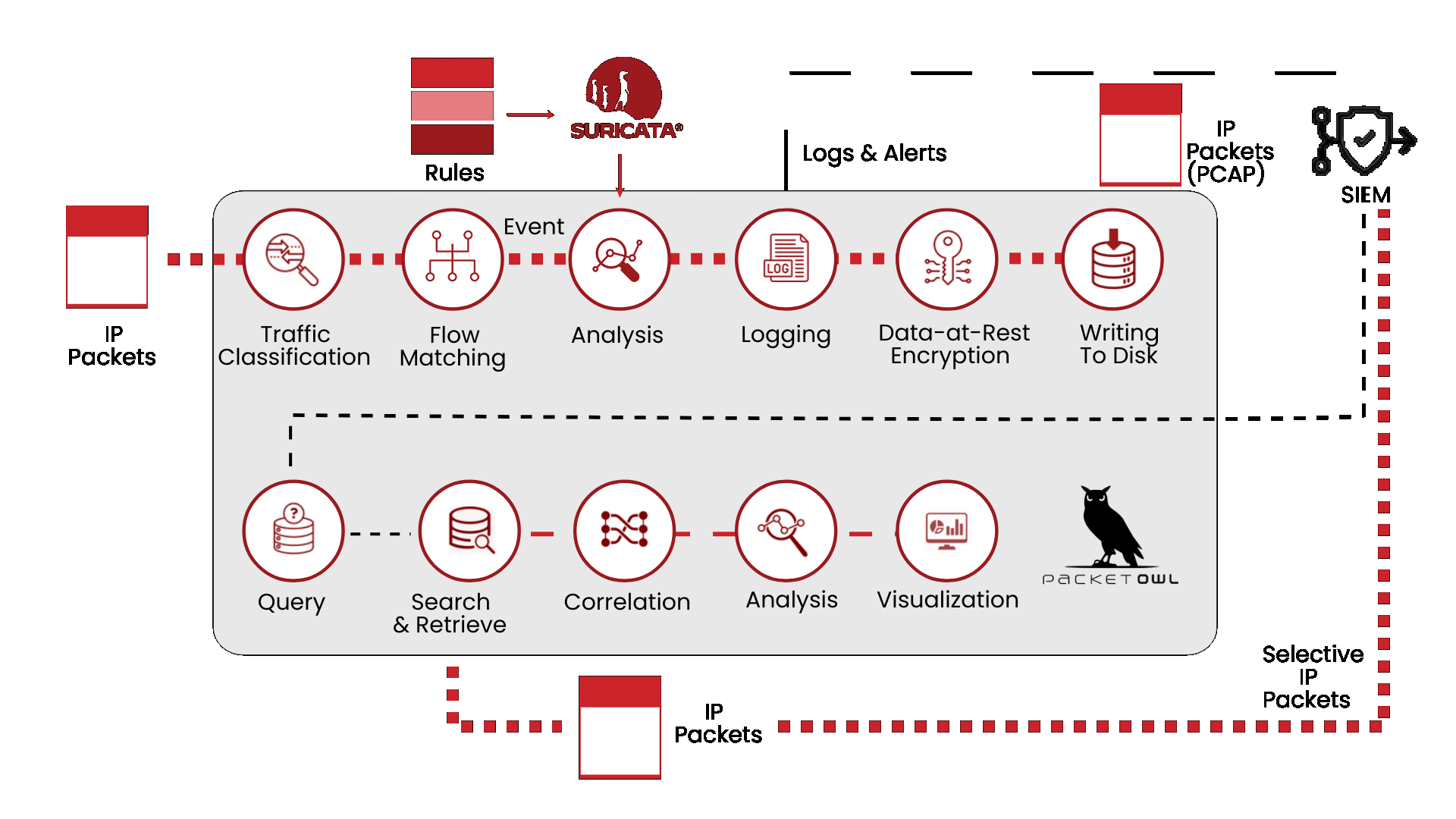
YOU CAN’T CONTROL WHAT YOU CAN’T SEE
Network Packet Data Never Lies. Get the Bottomline Truth
FEATURED CONTENT
Creating Solutions for Your Success

Solution Brief
NEOX & STAMUS Clear NDR

E-Book
Safeguarding Industrial Operations

Product Brochure
A Complete Guide to Products
Need to Discuss A New Project?
Whether you are building an Observability or Security practice ground up or refreshing and evaluating alternatives to your current solution, NEOX should be your list.











