Neox Networks Learning: Mastering Network Packet Capture and Analysis
Network Packet Capture (often referred to as PCAP) is the foundational practice of intercepting and logging the individual units of data (packets) that cross a computer network. As the ultimate source of truth, capturing network packets provides granular, indisputable evidence of everything happening on your network, making it essential for security, troubleshooting, and compliance. The ability to successfully record network traffic and perform deep-dive network packet analysis is what separates expert network engineers and security analysts from the rest.
What is an IP Packet?
To master packet capture, you must first understand its core element — the IP Packet, the basic unit of data transmitted over the internet or private networks. Every email, video, or file is split into packets at the source and reassembled at the destination.
A complete packet consists of two main parts:
The Header: Contains crucial metadata, including the source and destination IP addresses, port numbers, sequence numbers, and protocol information. The control layer that enables routing—like a mailing label on a letter. It tells routers where the packet came from and where it’s going. Key fields include:
- • Source IP Address: Sender’s address.
- • Destination IP Address: Recipient’s address.
- • Protocol Number: Identifies the Transport Layer protocol (e.g., TCP=6, UDP=17).
- • Time-to-Live (TTL): Limits how many hops a packet can make before being discarded.
The Payload: The actual application data being transmitted. By capturing these packets, you get visibility into both who is communicating (the header) and what they are communicating (the payload).The actual content—such as web data, audio, or file information. In packet analysis, the payload reveals what data was transmitted or accessed.
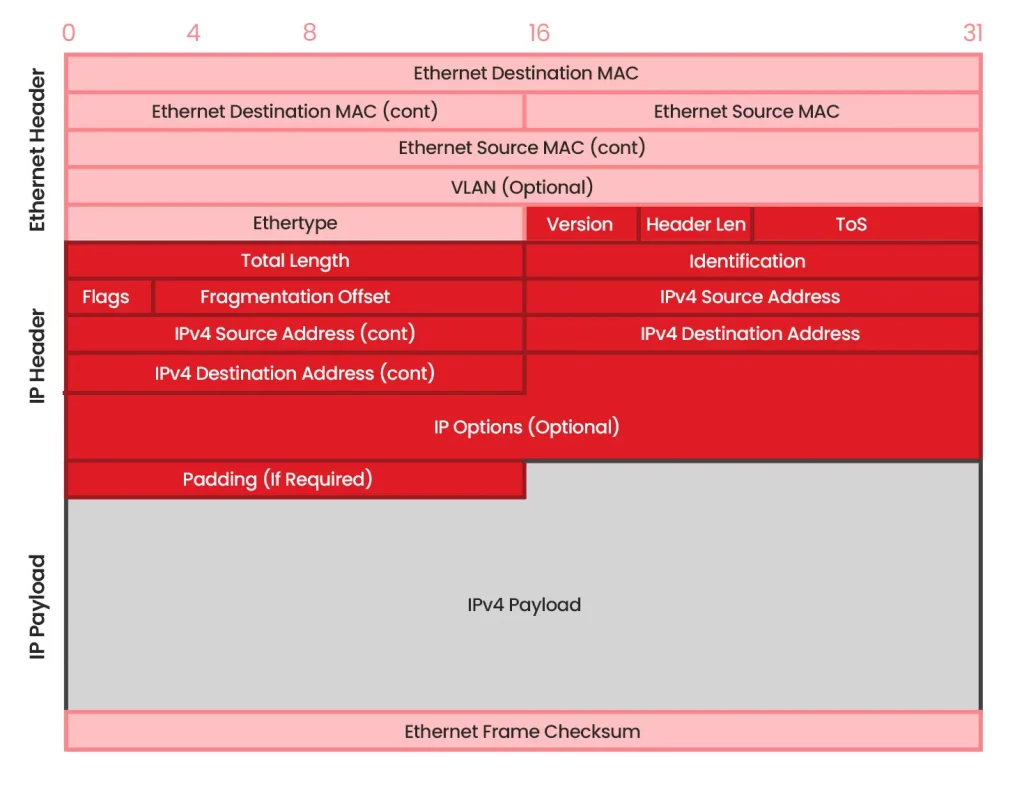
Diagram 1 : IP Table
What is Network Packet Capture?
At its core, network capture is the process of passively collecting a copy of the data stream flowing across a network link. When you view a web page, download a file, or send an email, that data is broken down into small, numbered packets.
The high-performance packet capture-to-disk (CTD) process consists of multi-component hyper-converged specialized hardware, so no packets are missed. The packets are captured by an FPGA-based specialized NIC (Network Interface Card), referred to here as SmartNIC. SmartNIC holds the packets and relays those to the processing logic, where packets are mapped to different streams and filtering and other criteria are applied. The full packets with the header and payload are then written to the spinning disks or solid-state drives (SSD) and indexed to be found later.
The process involves marvelous engineering to not drop a single packet despite the speed differential between the external network speeds (such as 100Gbps), capture speed, and then writing to the disk speed.
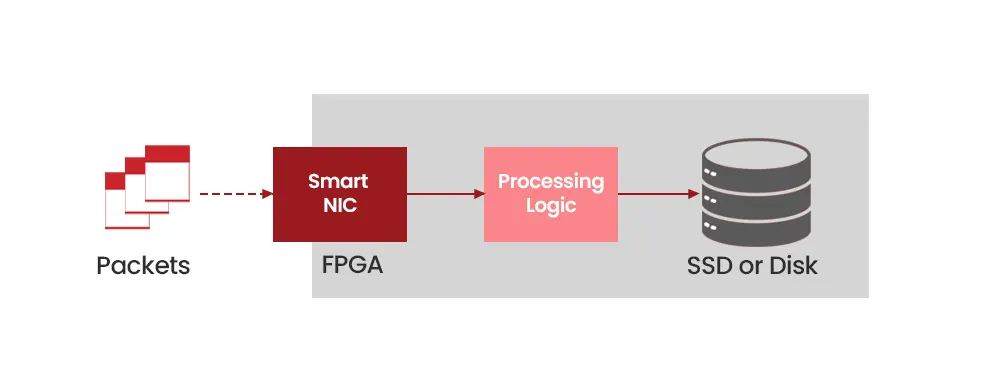
Diagram 2 : Capture to Disk Process
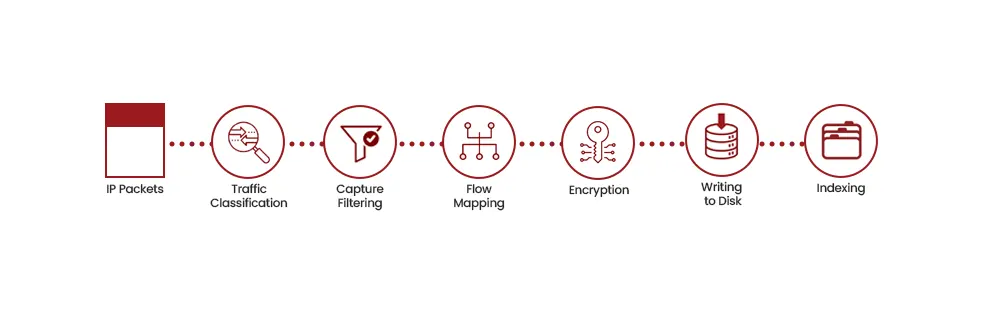
Diagram 3 : Capture to Disk Flow
When it’s time to search and retrieve the relevant packets in case of a troubleshooting event or security incident, you can send a query to the system to find the right packets from millions of packets based on prescribed criteria. The indexed packet data is searched, and the relevant packets can be downloaded and viewed directly from storage. Industry standard tools such as Wireshark can be used to view the packets, and the packets can be downloaded to the local laptop (which has performance limitations and is not recommended). Specialized capture appliances such as NEOX PacketFalcon and PacketGrizzly do not require downloading packets and provide enterprise-grade analysis software to analyze the packet data.
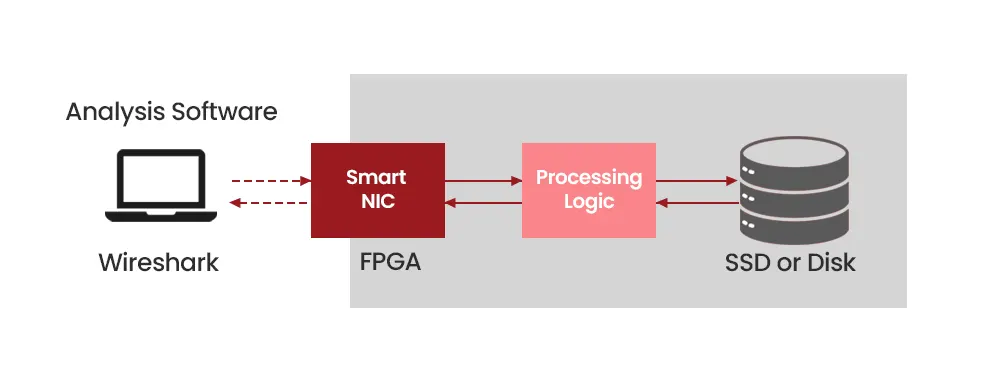
Diagram 4 : Packet Search and Retrieval Process
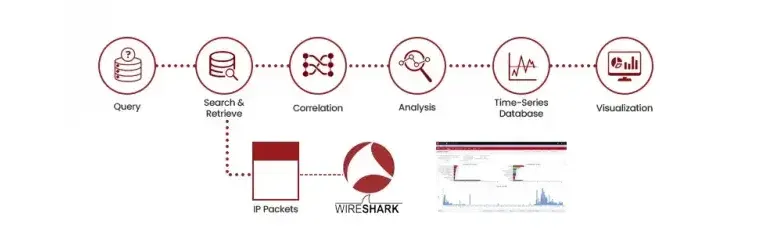
Diagram 5 : Packet Search and Retrieval Flow
Why Perform Network Packet Capture and Analysis?
Performing network packet capture and analysis transforms reactive firefighting into proactive problem-solving. It is the only way to get true, forensic visibility into network activity. Packet capture tools intercept and log these packets for analysis.
- • Troubleshooting: Inspecting headers helps confirm routing, detect latency, or find retransmissions.
- • Security: Examining payloads exposes malware, data leaks, or attacker activity.
| Use Case | Description |
| Network Troubleshooting | Diagnose intermittent performance issues, spot network congestion, latency issues, pinpoint packet loss, and verify Quality of Service (QoS) settings by analyzing TCP/IP handshake timings and retransmissions. |
| Cybersecurity & Forensics | Investigate a security incident. Logs only tell you what happened; packets show you how it happened. Analysts use PCAP files to reconstruct an attack, trace an attacker’s lateral movement, and identify data exfiltration. |
| Application Performance | Determine if application slowness is due to the network, the server, or the application itself (the classic “network vs. application” debate). |
| Compliance & Audit | Demonstrate compliance with internal or regulatory data retention policies by maintaining a forensic record of specific network segments or perimeters. |
Methods for Capturing Network Traffic
To capture network traffic effectively, you must position your capture solution at a strategic point in the network. There are two primary techniques used to access and capture traffic on network links:
(a). Port Mirroring (SPAN Ports)
- Pros: Cost-effective and instant solution, uses existing network hardware. May work for ad-hoc short-term capture, analysis, and troubleshooting at low network speeds.
- Cons: Can be unreliable under heavy load, as the switch prioritizes operational traffic over mirrored traffic, leading to dropped packets and an incomplete capture, as well as jeopardizing the switch’s performance for its primary forwarding role. Insecure and a security vulnerability, as attackers can use the SPAN port to enter the main data stream and breach the systems from there. Never a scalable or long-term solution.
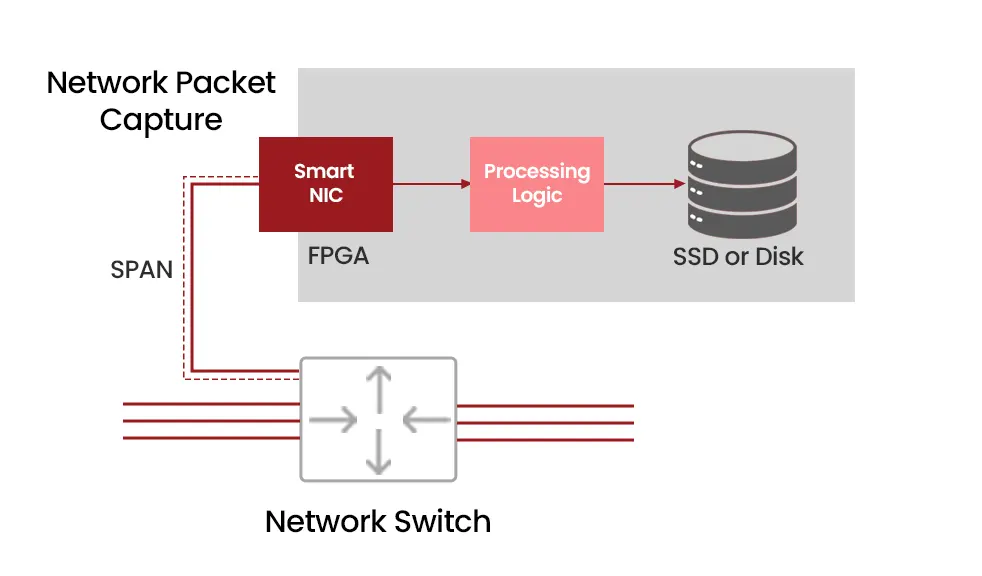
Diagram 6 : Capture Through a SPAN Port
(b). Network TAPs (Test Access Points)
- Pros: Provides a 100% complete copy of traffic (for full packet capture) from the wire and is completely fail-safe. Provides the highest performance at high network speeds without missing any packets, and is a long-term scalable solution for monitoring. Does not have any MAC or IP address of itself, hence cannot be detected or hacked. Active TAPs and Secure Fiber TAPs also have a data diode functionality, so reverse-path hacking is impossible, making it an extremely secure solution.
- Cons: Requires physical installation and dedicated hardware up front, and may need some rewiring and space.
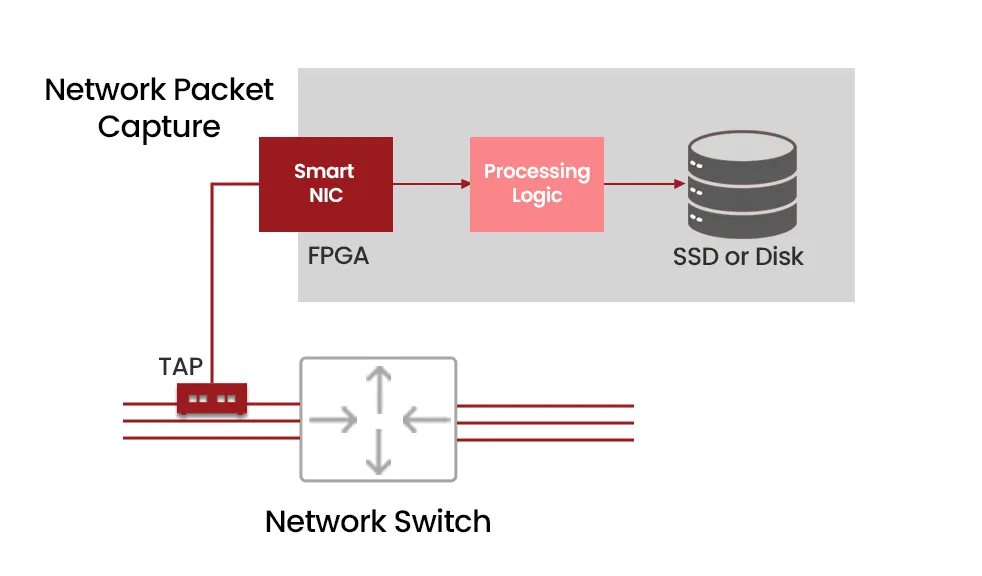
Diagram 7 : Capture Through a TAP
(c). Network Packet Broker
- Pros: A highly scalable and efficient way to consolidate the right network traffic and provides full control over when to turn off or on a data stream to a destination, or filter based on multiple criteria. Increases the capture device versatility as multiple sources can now be captured, and increases the capture storage capacity through filtering and deduplication types of features.
- Cons: Initial one-time setup and wiring, and some costs involved for an additional device, but the pros outweigh the cons.
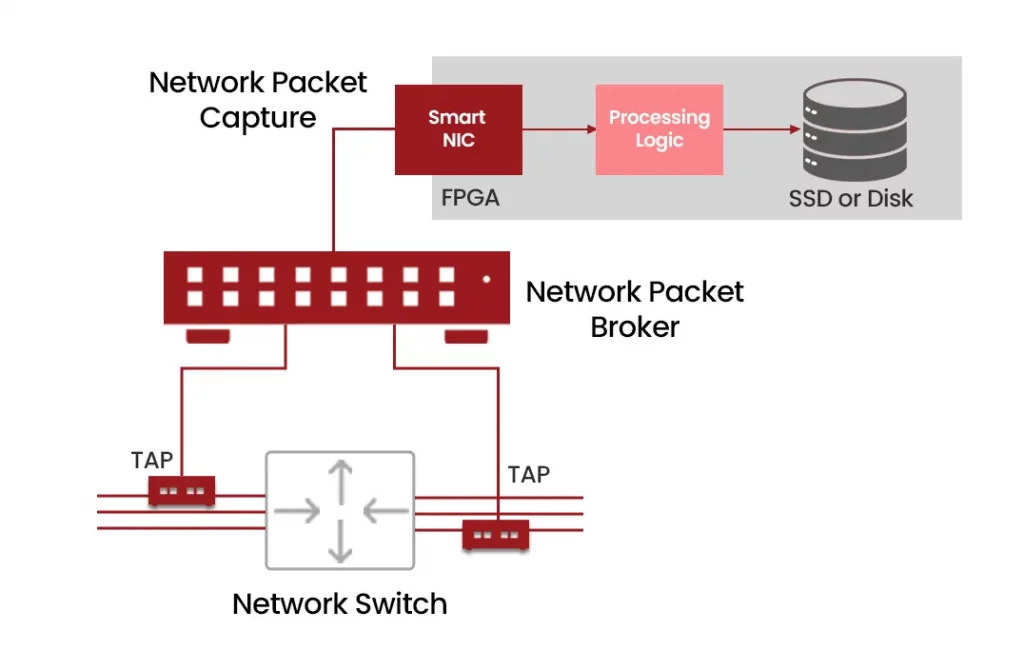
Diagram 8 : Capture Through a Packet Broker
Capture Tools: Software vs. Dedicated Appliance
The sheer volume and speed of modern network data require specialized packet capture tools to handle the load and process the information. It’s simply beyond software or CPU-based systems to handle it, and you need specialized FPGA-based systems to assure a lossless capture.
(a). Packet Capture Software
For small-scale, on-demand diagnostics, packet capture software installed on a host machine may work in some situations. For example, Wireshark is the industry-standard, free, and open-source packet capture tool (also called a protocol analyzer). It allows users to browse and filter captured data stored in PCAP files. It may work in situations where you are trying to troubleshoot a local WiFi issue or a remote brand office connectivity issue at under 10Gbps. However, the need to download packets to the local host machine, consumingstorage and opening up security and privacy vulnerabilities, as well as not being capable of handling high speeds such as 100Gbps, makes it unsuitable for anyserious enterprise or service provider network monitoring.
There are also virtualized versions of packet capture applications that are designed for on-prem virtual (VM) environments and for the cloud. These virtual appliances leverage the technology and work like the hardware appliance (below), but at a smaller scale and depend on the resources allocated in the cloud.
Diagram 9 : Packet Capture Software
(b). Packet Capture Hardware
For continuous, high-speed enterprise-scale packet capture and analysis, a dedicated packet capture appliance is required. These are high-performance hyperconverged systems designed specifically to handle massive volumes of network traffic without dropping a single packet (zero-loss capture). These specialized devices, sometimes simply called packet analyzers, are deployed at critical network points (like the internet perimeter or data center core) and offer handling 10, 25, 40, or 100Gbps capture-to-disk rates with massive packet storage capacities that range from Terabytes to Petabytes.The onboard or external expandable storage is either spinning disk-based or newer solid-state (SSD) based, and specialized encrypted storage (SED) is also an option for increased security and privacy for sensitive data center deployments. Intelligent features, such as filtering, allow you to capture only metadata or specific application traffic to conserve theexpensive disk space.
NEOX PacketFalcon and PacketGrizzly packet capture applications are such packet capture solutions offering up to 100Gbps of sustained full packet capture and up to 8 Petabytes of storage capacity.

Diagram 10 : Packet Capture Hardware
Network Analysis and Forensics
Packet capture is just half the job. Eventually, a network or security engineer or analyst would like to leverage the packet data and the metadata extracted from it for troubleshooting the network issues or for investigating a security incident, such as a breach. For such reasons, the PCAP data is almost always used with an Analysis Software that can read the data, extract and correlate the information out of it, and visualize it in an easy-to-consume graphical form.
Wireshark is an open-source software that is commonly used for analyzing packet data. But like many open source software, it has limitations. NEOX packet capture products support Wireshark but also ship with their own proprietary enterprise-grade analysis software. It can handle much higher performance and provides key metrics such as latency, top-talkers, protocol analysis, and additional insights for faster troubleshooting. Hence, the value of the packet capture solution is fully realized with such an analysis software, not by just having the hardware.
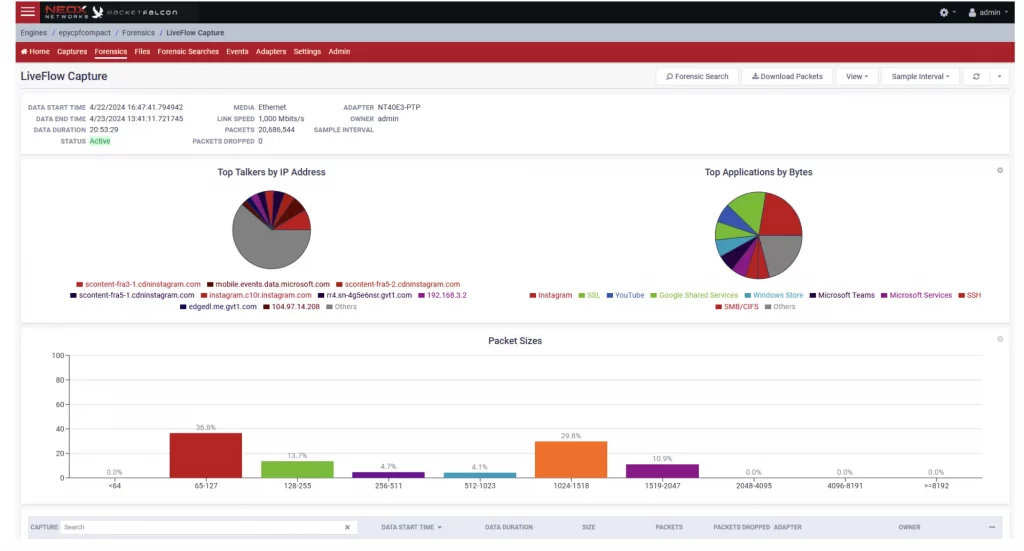
Diagram 11 : Network Analytics Example
FAQs
What is the primary purpose of network packet capture and analysis?
The main purpose is to gain deep, granular visibility into network activity. It allows IT teams to see the actual data—the headers and the payloads—of every communication. This is critical for:
- • Troubleshooting: Identifying the root cause of issues like latency, packet loss, or network congestion.
- • Security: Performing forensic analysis to understand how an intrusion occurred, what data was accessed, and the extent of the breach.
How do I capture traffic on network links without impacting performance?
The most reliable method is using a dedicated Network TAP (Test Access Point). Unlike SPAN/Mirror ports on a switch (which can drop packets), a TAP is a passive device placed in-line that creates a guaranteed, exact copy of the data stream without affecting the flow of live production traffic. This ensures you record network traffic with 100% fidelity.
Is Full Packet Capture always necessary?
Full Packet Capture (capturing both the header and the payload) provides the “ultimate truth” needed for deep forensic analysis. However, given the vast storage requirements, some organizations opt for Smart Packet Capture or filtered capture. This approach uses an network packet capture appliance to selectively record only the traffic relevant to a known issue (e.g., traffic to a specific IP address or protocol) or only capture the packet headers, which is often enough for performance monitoring and basic troubleshooting.
What are some common protocols that packet analyzers decode?
Packet analyzers are designed to decode hundreds of protocols across all layers of the OSI model. The most common protocols that are analyzed include:
- • Layer 2: Ethernet, ARP
- • Layer 3: IP (IPv4, IPv6)
- • Layer 4: TCP, UDP, ICMP
- • Layer 7 (Application): HTTP/HTTPS, DNS, SMTP, FTP, and proprietary application protocols.

